Craigslist × an Error Has Occurred. Please Try Again Later Proxy
This browser is no longer supported.
Upgrade to Microsoft Edge to accept advantage of the latest features, security updates, and technical support.
Troubleshoot Application Proxy problems and error messages
When troubleshooting Application Proxy issues, we recommend you start with reviewing the troubleshooting flow, Debug Application Proxy Connector issues, to determine if Application Proxy connectors are configured correctly. If you lot're withal having problem connecting to the application, follow the troubleshooting flow in Debug Application Proxy application issues.
If errors occur in accessing a published awarding or in publishing applications, check the following options to see if Microsoft Azure Advert Application Proxy is working correctly:
- Open the Windows Services console. Verify that the Microsoft AAD Application Proxy Connector service is enabled and running. You may also want to expect at the Application Proxy service backdrop page, as shown in the following prototype:
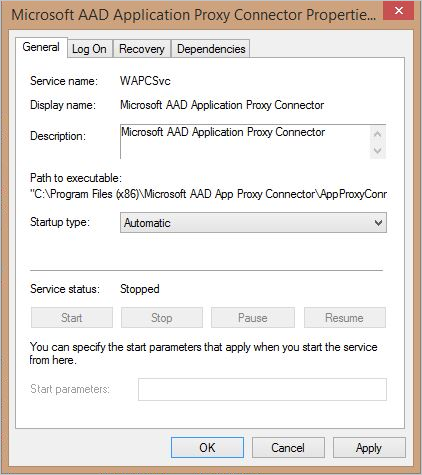
- Open Issue Viewer and look for Application Proxy connector events in Applications and Services Logs > Microsoft > AadApplicationProxy > Connector > Admin.
- If needed, more detailed logs are bachelor past turning on the Application Proxy connector session logs.
The page is not rendered correctly
You may accept issues with your application rendering or functioning incorrectly without receiving specific fault letters. This can occur if you published the article path, but the application requires content that exists exterior that path.
For instance, if you lot publish the path https://yourapp/app only the application calls images in https://yourapp/media, they won't be rendered. Make sure that y'all publish the awarding using the highest level path you need to include all relevant content. In this example, it would be http://yourapp/.
Connector errors
If registration fails during the Connector wizard installation, there are two ways to view the reason for the failure. Either expect in the event log under Windows Logs\Awarding (filter by Source = "Microsoft AAD Awarding Proxy Connector" , or run the following Windows PowerShell command:
Go-EventLog awarding –source "Microsoft AAD Awarding Proxy Connector" –EntryType "Fault" –Newest 1 Once you find the Connector mistake from the event log, use this table of common errors to resolve the problem:
| Mistake | Recommended steps |
|---|---|
| Connector registration failed: Brand certain you enabled Application Proxy in the Azure Direction Portal and that you entered your Active Directory user name and password correctly. Error: '1 or more errors occurred.' | If yous closed the registration window without signing in to Azure Advertizement, run the Connector magician again and register the Connector. If the registration window opens and and then immediately closes without assuasive y'all to log in, you'll probably get this error. This error occurs when there is a networking fault on your system. Make certain that it's possible to connect from a browser to a public website and that the ports are open equally specified in Application Proxy prerequisites. |
| Clear error is presented in the registration window. Cannot keep | If you see this error and then the window closes, you entered the incorrect username or password. Try again. |
| Connector registration failed: Make sure y'all enabled Awarding Proxy in the Azure Management Portal and that you entered your Active Directory user name and countersign correctly. Mistake: 'AADSTS50059: No tenant-identifying data institute in either the request or implied past whatever provided credentials and search by service principal URI has failed. | You're trying to sign in using a Microsoft Account and not a domain that is part of the organization ID of the directory you're trying to access. Brand sure that the admin is part of the same domain proper name as the tenant domain, for example, if the Azure Advertizement domain is contoso.com, the admin should be admin@contoso.com. |
| Failed to retrieve the electric current execution policy for running PowerShell scripts. | If the Connector installation fails, cheque to make sure that PowerShell execution policy isn't disabled. ane. Open the Group Policy Editor. |
| Connector failed to download the configuration. | The Connector's client certificate, which is used for authentication, expired. This may also occur if y'all take the Connector installed behind a proxy. In this example, the Connector cannot access the Internet and will not be able to provide applications to remote users. Renew trust manually using the Register-AppProxyConnector cmdlet in Windows PowerShell. If your Connector is behind a proxy, information technology is necessary to grant Net access to the Connector accounts "network services" and "local system." This can be accomplished either by granting them access to the Proxy or past setting them to featherbed the proxy. |
| Connector registration failed: Make sure yous are an Application Administrator of your Agile Directory to annals the Connector. Error: 'The registration request was denied.' | The alias you're trying to log in with isn't an admin on this domain. Your Connector is ever installed for the directory that owns the user's domain. Make sure that the admin account you're trying to sign in with has at to the lowest degree awarding administrator permissions to the Azure AD tenant. |
| The Connector was unable to connect to the service due to networking issues. The Connector tried to admission the following URL. | The connector is unable to connect to the Application Proxy cloud service. This may happen if you accept a firewall dominion blocking the connection. Make sure that you accept immune access to the right ports and URLs listed in Application Proxy prerequisites. |
Kerberos errors
This table covers the more common errors that come from Kerberos setup and configuration, and includes suggestions for resolution.
| Error | Recommended steps |
|---|---|
| Failed to retrieve the current execution policy for running PowerShell scripts. | If the Connector installation fails, bank check to make sure that PowerShell execution policy is not disabled. 1. Open the Group Policy Editor. |
| 12008 - Azure Advertizing exceeded the maximum number of permitted Kerberos authentication attempts to the backend server. | This mistake may signal incorrect configuration betwixt Azure AD and the backend application server, or a problem in time and date configuration on both machines. The backend server declined the Kerberos ticket created by Azure AD. Verify that Azure Advertisement and the backend application server are configured correctly. Make certain that the time and date configuration on the Azure AD and the backend awarding server are synchronized. |
| 13016 - Azure AD cannot retrieve a Kerberos ticket on behalf of the user because at that place is no UPN in the edge token or in the access cookie. | There is a trouble with the STS configuration. Fix the UPN merits configuration in the STS. |
| 13019 - Azure AD cannot retrieve a Kerberos ticket on behalf of the user because of the following general API mistake. | This consequence may indicate wrong configuration between Azure Advertising and the domain controller server, or a trouble in time and engagement configuration on both machines. The domain controller declined the Kerberos ticket created by Azure AD. Verify that Azure Ad and the backend application server are configured correctly, especially the SPN configuration. Make sure the Azure AD is domain joined to the aforementioned domain every bit the domain controller to ensure that the domain controller establishes trust with Azure AD. Make sure that the fourth dimension and date configuration on the Azure Advertizement and the domain controller are synchronized. |
| 13020 - Azure AD cannot retrieve a Kerberos ticket on behalf of the user considering the backend server SPN is not defined. | This event may indicate incorrect configuration between Azure Advertizing and the domain controller server, or a trouble in time and engagement configuration on both machines. The domain controller declined the Kerberos ticket created by Azure AD. Verify that Azure AD and the backend awarding server are configured correctly, especially the SPN configuration. Make sure the Azure AD is domain joined to the same domain as the domain controller to ensure that the domain controller establishes trust with Azure AD. Make certain that the time and appointment configuration on the Azure Ad and the domain controller are synchronized. |
| 13022 - Azure Advertizement cannot authenticate the user considering the backend server responds to Kerberos authentication attempts with an HTTP 401 error. | This consequence may betoken incorrect configuration between Azure Advertizement and the backend application server, or a problem in time and date configuration on both machines. The backend server declined the Kerberos ticket created by Azure AD. Verify that Azure AD and the backend application server are configured correctly. Make sure that the time and date configuration on the Azure AD and the backend application server are synchronized. For more information, see Troubleshoot Kerberos Constrained Delegation Configurations for Application Proxy. |
Terminate-user errors
This listing covers errors that your end users might see when they effort to access the app and fail.
| Fault | Recommended steps |
|---|---|
| The website cannot display the folio. | Your user may get this fault when trying to access the app you published if the application is an IWA application. The defined SPN for this application may be incorrect. For IWA apps, brand sure that the SPN configured for this application is correct. |
| The website cannot display the folio. | Your user may become this error when trying to access the app you published if the application is an OWA awarding. This could be acquired past 1 of the post-obit: |
| This corporate app can't be accessed. Y'all are non authorized to access this application. Authorization failed. Make sure to assign the user with admission to this application. | Your user may go this error when trying to access the app yous published if they use Microsoft accounts instead of their corporate account to sign in. Guest users may also get this mistake. Microsoft Account users and guests cannot access IWA applications. Make sure the user signs in using their corporate business relationship that matches the domain of the published application. You may non have assigned the user for this application. Go to the Application tab, and under Users and Groups, assign this user or user group to this application. |
| This corporate app tin can't exist accessed right now. Please endeavour again later…The connector timed out. | Your user may get this error when trying to access the app you published if they are not properly divers for this application on the on-premises side. Make sure that your users have the proper permissions as defined for this backend application on the on premises car. |
| This corporate app tin can't exist accessed. You are non authorized to access this awarding. Dominance failed. Make sure that the user has a license for Azure Active Directory Premium. | Your user may get this error when trying to access the app you published if they weren't explicitly assigned with a Premium license by the subscriber's administrator. Get to the subscriber'south Active Directory Licenses tab and make certain that this user or user group is assigned a Premium license. |
| A server with the specified host name could non be establish. | Your user may get this error when trying to admission the app yous published if the application's custom domain is not configured correctly. Make sure you've uploaded a certificate for the domain and configured the DNS record correctly by following the steps in Working with custom domains in Azure AD Application Proxy |
| Forbidden: This corporate app tin't be accessed OR The user could not be authorized. Make sure the user is divers in your on-bounds Advert and that the user has access to the app in your on-premises AD. | This could be a trouble with access to say-so information, see Some applications and APIs require access to authorization information on account objects. In a nutshell, add the app proxy connector auto account to the "Windows Dominance Access Group" builtin domain group to resolve. |
Encounter also
- Enable Application Proxy for Azure Agile Directory
- Publish applications with Application Proxy
- Enable single sign-on
- Enable Conditional Access
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-troubleshoot
0 Response to "Craigslist × an Error Has Occurred. Please Try Again Later Proxy"
Post a Comment